In this articles, how to install and configuration openldap in centos 6 step by step. openldap run 2 port: 389 ( insecure ) and 636 ( secure )
OU = Organizational Unit
DC = Domain infoponent
Step 3: Edit the following file:
Create it manually or use migration tools to automation
I use tool to create .ldif file :
Now generate a base.ldif file for your Domain, use the following:
Copyright by: www.linuxoperatingsystem.info http://goo.gl/kMscJ4
Read More...
What does CN, OU, DC mean?
CN = infomon NameOU = Organizational Unit
DC = Domain infoponent
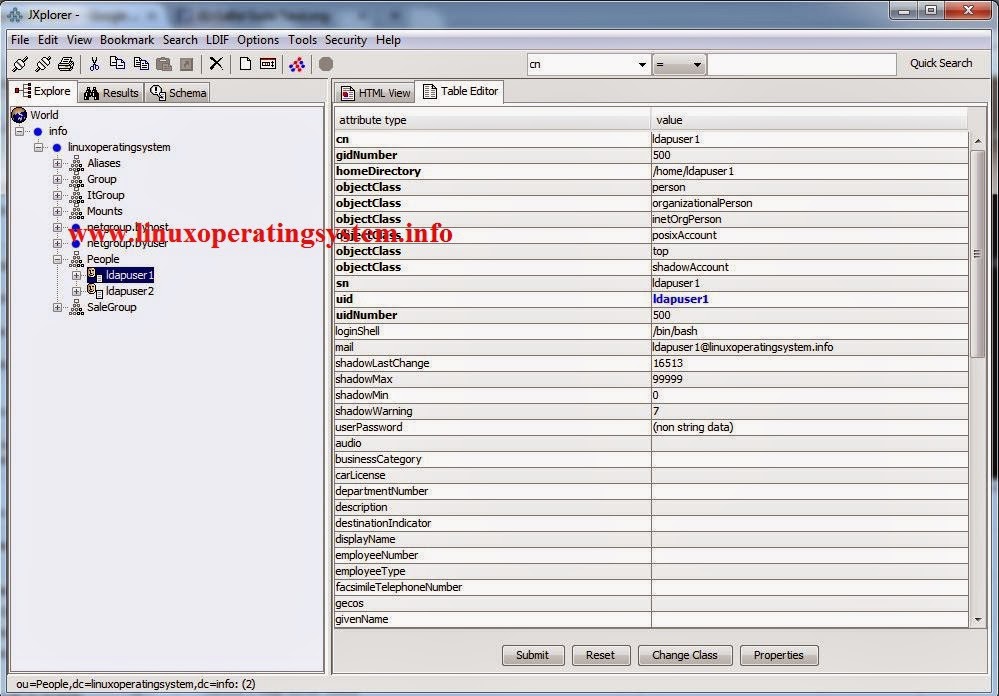
Installing and configuration openldap server on in centos 6
Step 1: Install LDAP# yum install openldap*Step 2: Now generate a encrypted password for Administrator User That is "Admin"
# slappasswdNOTE: You need to copy above generated password to text
Step 3: Edit the following file:
# vi /etc/openldap/slapd.d/"cn=config"/"olcDatabase={2}bdb.ldif"Change
olcSuffix: dc=linuxoperatingsystem,dc=infoStep 4: Now specify the Monitoring privileges
olcRootDN: cn=Admin,dc=linuxoperatingsystem,dc=info
olcRootPW: <paste encrypted="" here="" password="" your=""> ( copy password at step 2 )
olcTLSCertificateFile: /etc/pki/tls/certs/linuxoperatingsystem.pem
olcTLSCertificateKeyFile: /etc/pki/tls/certs/linuxoperatingsystemkey.pem
# vi /etc/openldap/slapd.d/"cn=config"/"olcDatabase={1}monitor.ldif"Chage
"cn=manager,dc=linuxoperatingsystem,dc=info"to
"cn=Admin,dc=linuxoperatingsystem,dc=info"Step 5: Now copy the sample database file
#cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIGStep 6: Configure OpenLDAP to listen on SSL/TLS
#chown -R ldap:ldap /var/lib/ldap/
# vi /etc/sysconfig/ldapStep 7: Now you need to create a certificate for OpenLDAP Server.
SLAPD_LDAPS=yes #(default is no)
# openssl req -new -x509 -nodes -out /etc/pki/tls/certs/linuxoperatingsystem.pem -keyout /etc/pki/tls/certs/linuxoperatingsystemkey.pem -days 365Step 8:You need to change owner and group ownership of certificate and keyfile
#chown -Rf root:ldap /etc/pki/tls/certs/linuxoperatingsystem.pemStep 9: Start/Restart the service of OpenLDAP
#chown -Rf root:ldap /etc/pki/tls/certs/linuxoperatingsystemkey.pem
# service slapd restartStep 10: Now you need to create base objects in OpenLDAP.
# chkconfig slapd on
Create it manually or use migration tools to automation
I use tool to create .ldif file :
# yum install migrationtoolson the Line Number 61, change "ou=Groups"
# cd /usr/share/migrationtools/
# ls
# vi migrate_common.ph
$NAMINGCONTEXT{'group'} = "ou=Groups";on the Line Number 71, change your domain name
$DEFAULT_MAIL_DOMAIN = "linuxoperatingsystem.info";on the line number 74, change your base name
$DEFAULT_BASE = "dc=linuxoperatingsystem,dc=info";on the line number 90, change schema value
$EXTENDED_SCHEMA = 1;For example: Creating 2 local users and groups and then I will migrate to LDAP
# useradd -d /home/ldapuser1 ldapuser1Now assign the password
# useradd -d /home/ldapuser2 ldapuser2
# passwd ldapuser1Now you need to filter out these users from /etc/passwd to another file:
# passwd ldapuser2
# getent passwd | tail -n 2 > /root/usersNow you need to filter out password information from /etc/shadow to another file:
# getent shadow | tail -n 2 > /root/passwordsNow you need to filter out user groups from /etc/group to another file:
# getent group | tail -n 2 > /root/groupsSo Open the following file to change the location of password file
# vi migrate_passwd.plInside this file search /etc/shadow and change it to /root/passwords and then save and exit.
Now generate a base.ldif file for your Domain, use the following:
#./migrate_base.pl > /root/base.ldifNow generate a ldif file for users
# ./migrate_passwd.pl /root/users > /root/users.ldifNow Generate a ldif file for groups
# ./migrate_group.pl /root/groups > /root/groups.ldifStep 11: Now it' time to upload these ldif file to LDAP Server
# ldapadd -x -W -D "cn=Admin,dc=linuxoperatingsystem,dc=info" -f /root/base.ldif
# ldapadd -x -W -D "cn=Admin,dc=linuxoperatingsystem,dc=info" -f /root/users.ldif
# ldapadd -x -W -D "cn=Admin,dc=linuxoperatingsystem,dc=info" -f /root/groups.ldif
Enable log openldap Server
# vi /etc/rsyslog.confAdd line following below into rsyslog.conf
# LDAPRestart Rsyslog server
local4.* /var/log/ldap.log
# /etc/init.d/rsyslog restart
Restart openldap server
# /etc/init.d/slapd restartNow you can use "ldapsearch" command
# ldapsearch -x -b "dc=linuxoperatingsystem,dc=info"



























%2Bubuntu%2B14.10.JPG)

